Following the introduction in “A Brief Discussion on the adoption of International Certification Standards for Cloud Service Information Security Management (Part I),” this article continues to share the standards regarding personal data protection in public cloud services and the specifications of cloud security certification launched by the Cloud Security Alliance; it also summarizes the key points of the aforementioned standards.
Personal Data Protection in Public Cloud Services (ISO/IEC 27018:2019)
Based on the operational specifications of the Information Security Management System (ISO/IEC 27001), there are 16 extended controls, and 25 additional control requirements derived from the privacy principles of the Privacy Framework (ISO/IEC 29100), totaling 41 items. These standard targets public cloud service personal data (PII) processors, requiring cloud service providers to manage the entire lifecycle of personal data processing, and emphasizes the obligations of personal data processing. It stipulates the control measures to be followed, including use for specific purposes, personal data protection mechanisms, storage location of personal data, change records, return and deletion of personal data. For example, cross-border transmission and storage locations of personal data are of great importance. Therefore, this standard’s privacy compliance control measures require public cloud personal data processors to clearly explain the possible countries where cloud service users’ personal data may be stored with supporting records provided as evidence.
Security, Trust & Assurance Registry (STAR)
This certification launched by the Cloud Security Alliance (CSA) is called the Security, Trust and Assurance Registry, abbreviated as CSA STAR. Its certification framework is divided into three levels, from self-assessment questionnaires and third-party certifications to continuous monitoring. To obtain the certification, it is necessary to use the Cloud Control Matrix (CCM) as a basis to check the information security management status of cloud service providers. The latest version currently covers 17 control domains, including human resources, application and interface security, change control and configuration management, data security and privacy lifecycle management, infrastructure and virtualization security, audit and assurance, governance, risk and compliance, cryptography and key management, data center security, logging and monitoring, identity and access management, threat and vulnerability management, security incident management, e-discovery and cloud forensics, business continuity management and operational resilience, interoperability and portability, unified endpoint management, supply chain management, and transparency and accountability. In total, there are 197 control items across these domains. Subsequently, the cloud security management status is evaluated according to a capability maturity model, with scores ranging from 1 to 15, corresponding to five levels of information security maturity: no formal method, reactive, proactive, managed, and optimized.
Summary of Key Points for the Introduction of Cloud International Standards
In summary, the comparison of the above three international standards focuses mainly on requirements for cloud service providers, with relatively less content directed at cloud service users. All are based on ISO 27001, and verification of that standard must be passed first. As the current ISO versions are not yet fully aligned, attention must be paid to the wording of the statement of applicability. In addition, when internal auditors conduct audits, they should first clarify the role of the audited unit to understand the responsibilities it should fulfill or delegate to others. In this way, appropriate reference standards can be selected. These are listed below.
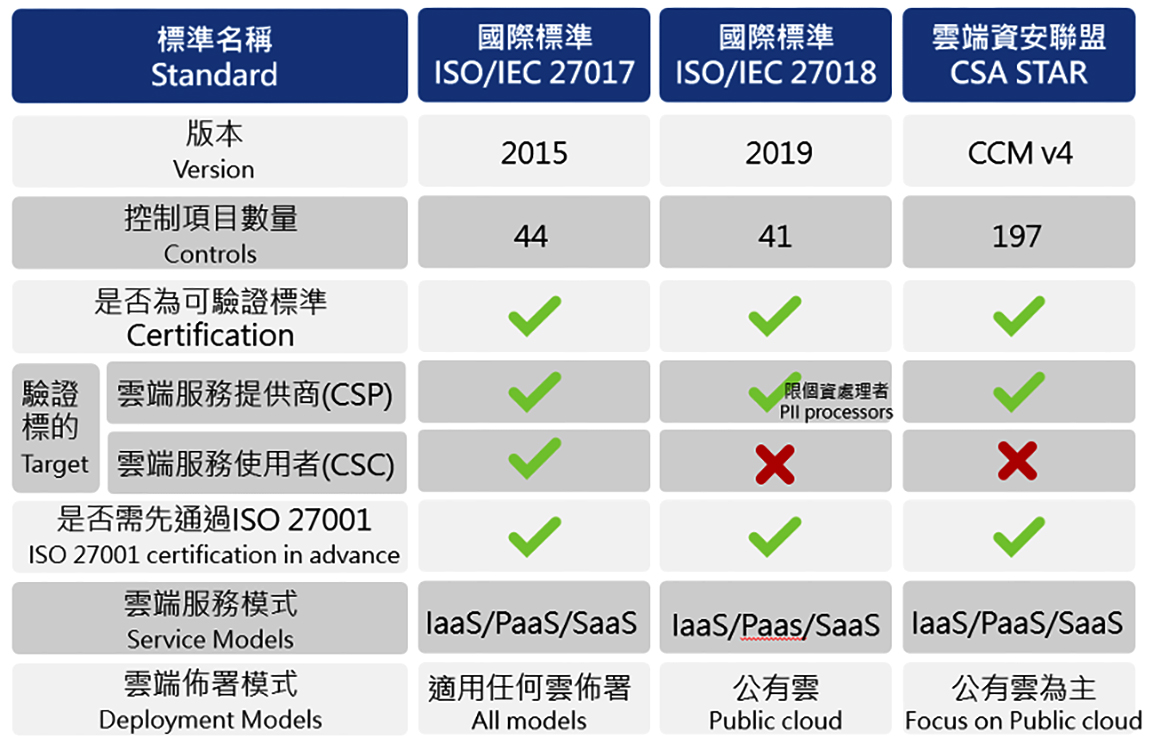
Table: Summary of Key Points of International Standards (Data source: Compiled by the Internal Auditing Department)
Conclusion
In light of enterprises’ increasing reliance on cloud computing and the ongoing rise in information security threats, it is advisable to refer to control measures from selected international standards or fully adopt international standards and achieve certification. This can help enterprises establish a solid cloud service information security management foundation. As of now, the TDCC is a cloud service user. Apart from audit work on external cloud service providers, the Internal Auditing Department will, when necessary, conduct project-based audits. At that time, in addition to referring to the above standards, attention will also be paid to monitoring and collecting information on the development of cloud computing applications as well as related risks and threats. These will serve as references for drafting audit plans and items to improve the company’s procedural guidelines. This is expected to contribute to their refinement, facilitate the implementation of information security operations, and effectively manage cloud-related security risks.

