Following the “Internal Audit Transformation: The Application of Information Security Audit Solutions” from the 271st issue of TDCC e-Bimonthly, this article continues to share our experiences in conducting Simulated Red Teaming in 2023. This exercise simulated cyberattacks on TDCC’s internet system. It focused on various attacks on information systems to verify the effectiveness of information security defenses. This allowed us to identify weaknesses in information security defenses more promptly while achieving the “effectiveness evaluation of information security monitoring and protection encouragement” of Financial Cyber Security Action Plan 2.0.
1.Simulated Red Teaming
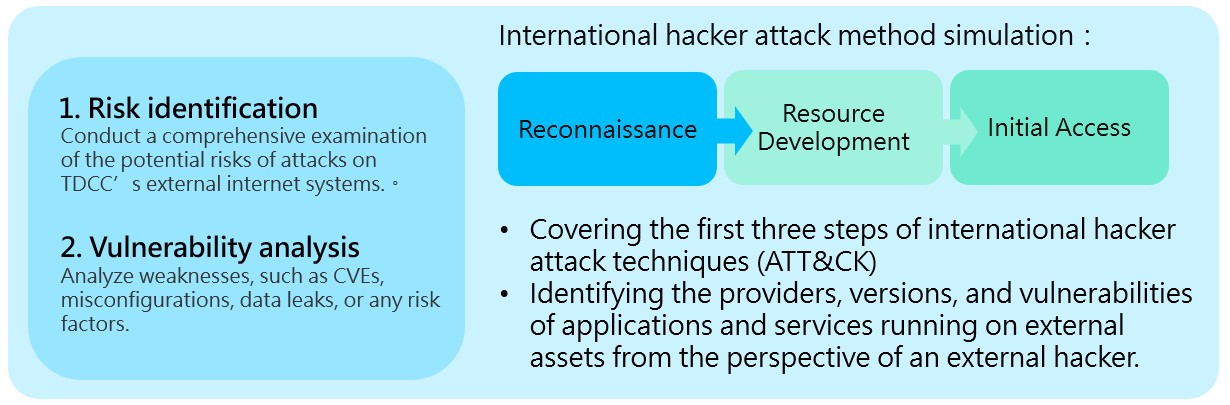
We adopted the ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) information security framework launched by MITRE to ensure effective communication between the offense and defense during the exercise. This allowed the invasion process of the attacker to be corresponded and helped us better understand the strategies, techniques, and potential security risks to information security, thereby improving our information security defense mechanisms. Simulated Red Teaming was executed in two stages. The first stage involved reconnaissance and scanning. Attack Surface Management (ASM) tools were used to simulate hackers’ silent exploration and vulnerability hunting before actual attacks to identify system parameter configuration errors, sensitive information leakage, system version vulnerabilities, or oversight in management. The second stage included actual attacks. Breach and Attack Simulation (BAS) tools were utilized to simulate the full range of techniques of internationally known hacker groups, with scripts referencing past information security incidents to replicate their attack methods and steps. The tools performed precise and diversified attack and defense drills to verify whether information security defense devices (such as intrusion prevention systems, web application firewalls, endpoint detection and response) would trigger alerts and effectively block attacks. They could also provide us with an assessment of the overall protection situation and operational enhancement.
2.Phase one: attack surface management
Under the waves of digital transformation, enterprises possess a more extensive and diversified set of information assets, some of which are even deployed in cloud environments. However, in the cyberspace, any connection can become a target of attack or a gray area of management. This means that the channels susceptible to hacker attacks are also increasing, and the level of risk exposure is continuously rising. This stage employed attack surface management tools to constantly explore and scan our information assets exposed to the internet, such as websites, services, certificates, databases, virtual hosts, source code, etc., based on domain names. By detecting potential risks through these tools, vulnerabilities could be effectively discovered. Two cases found are shared in this article:
(i) Information systems exposed the specific cloud services and versions in use
Due to improperly adjustment of system parameters, specific cloud services and versions in use were exposed. This might result in hackers targeting the vulnerabilities of particular cloud service providers.
(ii) Information systems providing external services were no longer in use but had yet to be decommissioned
After the transition from old to new systems, the failure to decommission old systems promptly not only confused external users but might also neglect routine information security checks. This brought about medium to high-risk vulnerabilities in systems, which become targets for hacker attacks.
This stage helped us to take a more proactive and comprehensive grasp of the status of internet services, increase the visibility of information assets, identify unknown, unmanaged, or poorly managed information assets, discover their vulnerabilities, and carry out improvements and patches, thereby reducing information security risks.
3.Phase two: external intrusion and attack simulation
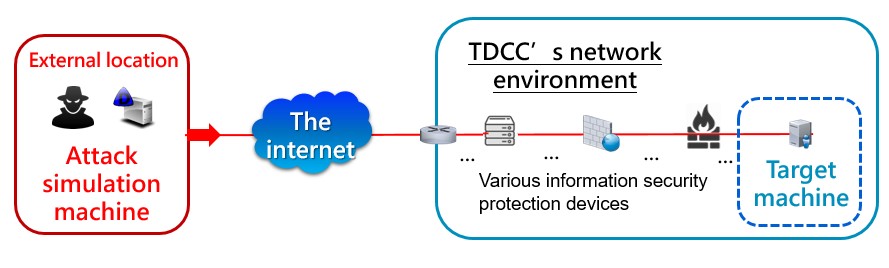
Previously, the execution of Red Teaming, information security health checks, penetration testing, vulnerability scanning, and other related security assessments depended heavily on a large professional workforce, and the previous experiences of the executors were especially valued. To elevate execution efficiency and reduce human operational errors, external intrusion and attack simulation tools were the solution to the problems mentioned above. This could achieve the automated simulation of hacker behavior and execute precise and real-time attack and defense drills.
A brief explanation of the attack and defense process (Figures 2 and 3) involved setting up a simulated attack host externally and target machines internally. The attack host executed attack procedures according to the arranged drill scripts, including various attack methods of internationally known hacker groups (such as financial hackers FIN 7, hacker organization APT 29) and Web OWASP Top Ten 2021. The process examined whether our layered information security defense equipment could effectively resist malicious attacks and promptly produce alert messages.
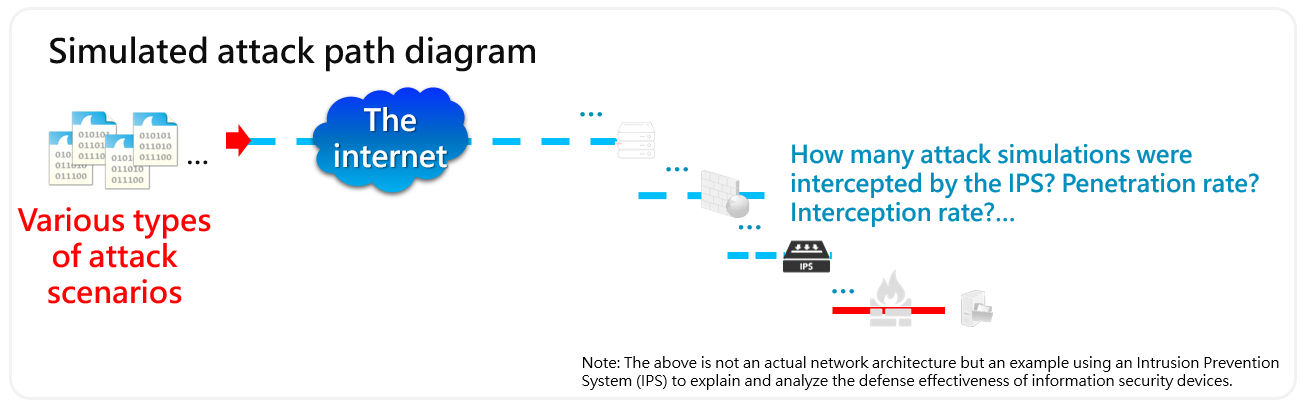
After the information security attack and defense drill, the author truly learned a lesson with key summaries as follows:
(i) Profound layered defense: achieving synergistic efficacy
To effectively utilize information security equipment’s capabilities, its characteristics should be considered and deployed in the most appropriate positions within the organization to allow each device to complement each other and jointly resist malicious attacks. Additionally, regardless of vulnerabilities in the application system (AP), operating system (OS), or tool software, priority should be given to processes such as upgrades, patches, or decommissioning and replacements. Relying on information security equipment protection is not a long-term solution.
(ii) Technical management: complementary support
The operation of information security equipment must be carefully assessed along with management regulations. For example, whether the insufficient equipment update frequency could lead to hackers exploiting zero-day vulnerabilities. Timely risk assessments should be conducted to find the most suitable methods for the organization’s daily operations and the balance between efficiency and security.
(iii) Supreme strategy: subduing the enemy and initiating the defense
The chapter “Attack by Stratagem” of The Art of War by Sun Tzu mentions, “The supreme art of war is to subdue the enemy without fighting. The next best is to disrupt their alliances, followed by attacking their army, and the last option is to besiege their cities.” The same principle applies to information security defense. Defenders must also possess an attacker’s mindset to understand what the attackers intend to do. In this way, defenders can preemptively adopt more proactive and aggressive defensive strategies and even deploy decoy systems to collect more information about the attackers. This can ultimately cause the attackers to give up their assault. Furthermore, intelligence should be appropriately utilized to timely strengthen defense mechanisms and test the effectiveness of information security protections in advance. This phase not only verifies the effectiveness of information security defense mechanisms but also achieves the following benefits:

4. Enrichment and enhancement
The Internal Auditing Department will continue to focus on applying various emerging technologies in information security. Continuing our commitment to corporate resilience and risk operation in digital service development, along with compliance audits, we will timely plan and arrange specific projects, cooperate with IT Departments, and implement as well as enhance the three lines of defense in information security.

